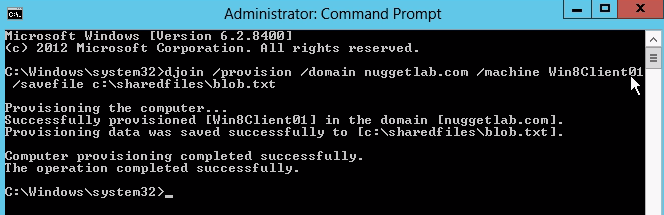
logging onto domain with user/pass creates secure channel
secure channel brokem (do not join workgroup then domain. creates new sid, lose group member)
- > 30day PW reset
- os reinstall
- LSA out of sync
fixes
- ADUC reset compute, rejoin
- DSMOD computer-reset, rejoin
- NLtest (no rejoin or reboot)
- powershell: test-coomputersecurechannel -repair
DSMOD command to reset computer acct
NLtest command to reset. issue on the PC
"server" is name of computer to reset computer acct
Powershell command. issue on the PC